Ransomware attacks are no longer a distant threat; they’re a daily reality. With businesses across every stage of the food supply chain held hostage by unseen groups. In less than ten minutes, a ransomware attack can bring a processing line to a halt, costing hundreds of thousands in lost output.
The risk of ransom attacks on businesses is nothing new, what has changed is the speed it can infiltrate a digital system and cause damage. What not long ago took days to accomplish, now happens in hours, with advancing artificial intelligence tools accelerating attack capability even more.
Prevention or payment: the ransomware economy
What is the risk of ignoring cybersecurity in food processing? A ransomware attack can shut down your production line in minutes.

How investing in cybersecurity today protects your business, your people, and the food supply chain tomorrow.

For food processors, it is no longer just data that needs protecting. Modern ransomware can shut down production lines, disrupt supply chains, and threaten food security. It is no longer a question of if your business will be targeted, but how prepared you are when it happens.
The good news is you don’t need abandon the advantages of digital systems that drive efficiency and competitiveness. You just need to understand the risks and invest in protection.
Understanding the enemy. What is ransomware?
In simple terms, ransomware is malicious software that locks down your computer systems and data. Bad actors (the criminal hackers) then demand payment – usually in cryptocurrency – to restore access. But modern extortion goes beyond encryption. Today’s attackers may:
- Sell stolen data on the dark web
- Threaten suppliers or customers using exfiltrated data
- Disrupt online services
- Leak sensitive information to manipulate stock prices
These tactics evolve rapidly, often powered by AI, making it essential to understand not just what ransomware is, but how it operates like a business, targeting vulnerabilities for maximum impact.
How modern attacks unfold
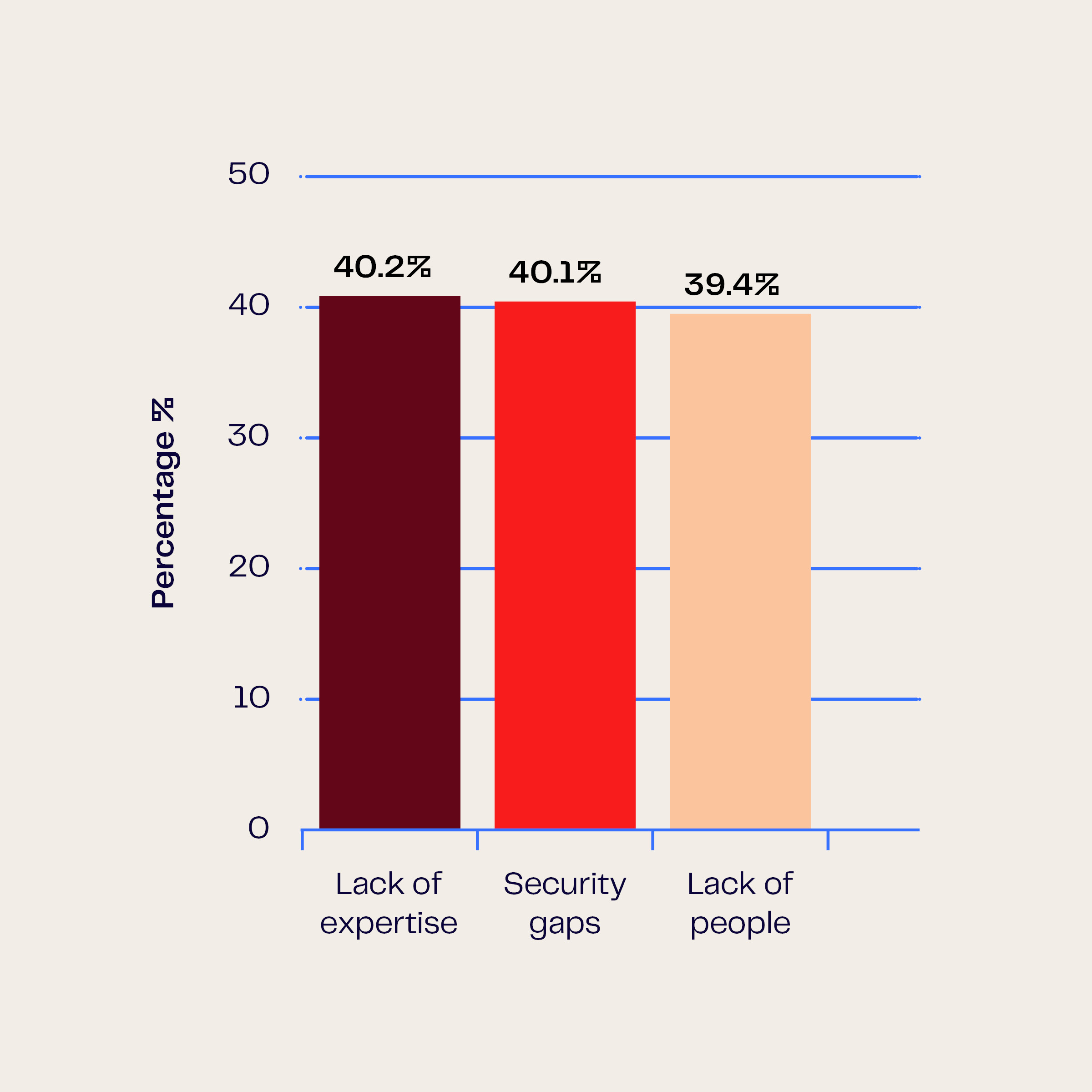
Today ransomware attacks operate like a sophisticated business. Criminal organizations deliberately target victims using a detailed, proven, playbook to maximize damage and profit. According to the 2025 Sophos State of Ransomware report, which surveyed 3,400 businesses across 17 countries, the most common factors – often in combination - leading to successful attacks are:
- Lack of expertise (40.2 %)
- Unknown security gaps (40.1 %)
- Lack of people/capacity (39.4 %)
The attack timeline

When the invisible becomes visible
There can be multiple factors why specific businesses are targeted for ransomware attacks, most commonly; financial gain, data value, and disruption—political or infrastructure. On the surface this seems to indicate larger businesses are more at risk, but small and mid-sized operations are increasingly falling victim to attacks due to weaker security defenses. They may offer smaller financial gains but, if security systems are weak, also require a shorter time investment. It is easy to imagine that if a larger business has weak defenses and the financial gain is substantial, they are the ideal target for ransomware attackers.
While attacks are invisible to everyone but IT teams, the repercussions are anything but.
Cybersecurity for small and mid-sized processors: Where to start
Small and mid-sized food processors often face tight margins and limited IT resources. But you can begin building resilience with minimum investment.
Concerned about your own production vulnerabilities?
Industry knowledge is crucial to understanding the security risks for food processors. JBT Marel works in partnership with processors to reduce vulnerabilities across IT and OT environments with the aim of ensuring continuity of operations. Explore how our systems support secure operations and contribute to a resilient food supply chain.
The human impact
Organizational psychologists studying the effect on employees and company culture have noted that the trauma of the event affects all employees, either directly or indirectly involved in the attack. For businesses this can result in teams falling apart in the months after the crisis, with members leaving or staying home on sick leave.
Direct reporting from companies who have experienced ransomware attacks, state there are always repercussions to employees whether in Leadership, IT or other teams:
- Increased anxiety or stress about future attacks
- Feelings of guilt
- Lasting fears about job stability
- Lasting fears about system security
- Increased pressure from senior leadership
- Staff absences due to mental health issues related to the attack
- Replacement of leadership teams

Many valuable team members resign after attacks, adding recruitment and training costs to an already expensive recovery. The invisible psychological impact rippling through the company culture long after systems are restored.
Multiple studies into the ransomware experience from an employee position, all point to three main factors which played a key role in making the experience better, or worse.
- Preparedness – crisis planning. Staff who have continuity plans and an understanding of likely impacts and workarounds respond better. As one IT Director said in an interview for a research article published in Journal of Cybersecurity, 2024, when asked about the importance of developing a business continuity plan before an attack, ‘You’ve not got the concept of no IT. There is no email. There is no Excel. Think pencil. Think paper.’
- Leadership culture – thoughtful leadership culture and a corporate understanding of the value of cyber security. Poorer outcomes tend to come from less experienced and robust leadership teams. Interviews conducted also note the stress of a ransomware attack exacerbates company culture, if morale is already low, the vulnerability of an attack can have a disproportionate effect, resulting in valuable team members leaving when the worst of the incident is over.
- Communication – rapid and effective communication channels. Between senior leadership and teams, and externally; to agencies, government bodies, suppliers, customers, and press. Depending on context, opacity or transparency for different communication strategies will be key to alleviating harm experienced by the business and teams. During the crisis having alternate systems planned and understood by staff will ensure crucial conversations can continue even if IT systems don’t. Effective communication goes beyond the crisis, and into recovery stages. Ensuring continued support and clearly defined learnings for all.
Why are food processors attractive targets?
The food supply chain is an ideal target for ransom attacks. Volatile products, complex supply chains, and critical demand for products ensure ransom demands will be acted on quickly to minimize damage and delays.
What makes today’s food processing facilities particularly vulnerable is the convergence of information technology (IT) systems with operational technology (OT) systems that control production equipment. The combination of old and new technologies is the dream for ransomware infiltrators:
- Legacy equipment with outdated security
- Connected systems that provide multiple entry points
- Critical operations that create pressure to pay ransoms quickly
- Supply chain dependencies that amplify disruption
The growing wave of cybersecurity threats and cybersecurity legislations mean it is essential for food processing providers to raise the standards of their security features to protect businesses, products and the food supply chain as a whole. At JBT Marel we see it as a responsibility to our customers to be leaders in this area. Going beyond regulatory requirements to ensure our solutions are enhancing cyber security to processing lines, IT areas, and businesses as a whole. JBT Marel’s digital cloud products have all achieved ISO/IEC 27001:2022, an internationally recognized standard for managing information security. This ensures our cloud-based systems meet rigorous security requirements and are continuously improved to stay ahead of evolving threats.
The difficulty of investment in the invisible
Food processors face relentless pressure on margins, regulatory compliance costs, and resource expenses. Investing in “invisible” cybersecurity seems less urgent than new equipment that immediately improves productivity and addresses labor shortages. This is especially true for small and mid-sized businesses (SMEs) where capital and operational expenditure is finite and choosing between fast ROIs and the ongoing expense of security for a problem you might never have is more difficult.
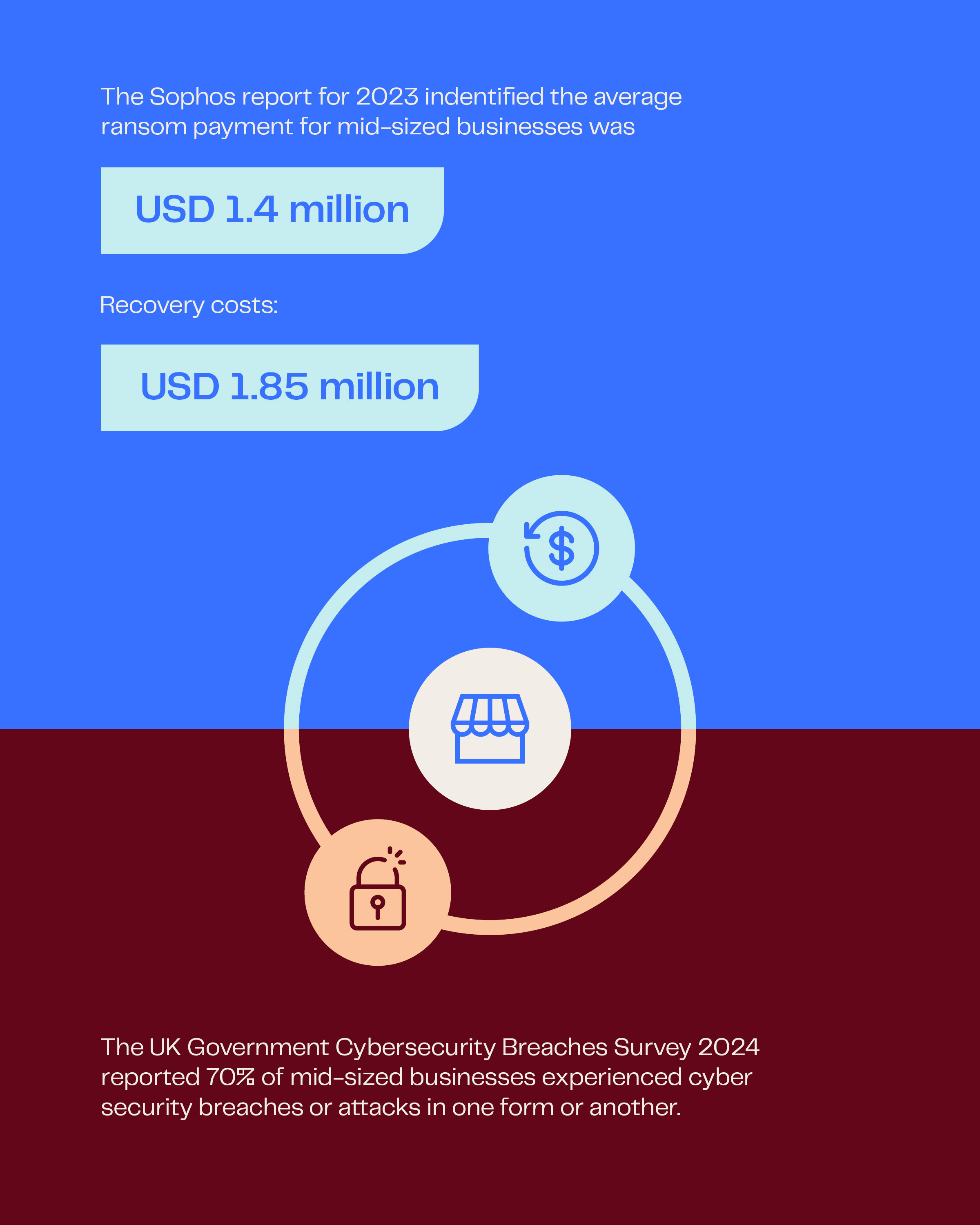
When calculated against the cost of building and maintaining a cybersecurity system, the very visible cost of loss resulting from cyber-attacks should be included in any capital and operational budgetary equations.

Louie Bardic, Director of Service for Software at JBT Marel, explains the practical approach, “It can be an effort to get security up to scratch for some businesses. When you start, usually “the house” is a little messy. But over time you build a more secure environment, and your costs should come down. Then it’s a matter of managing what you have in place. It’s hard to see it happening to your business, but if you don’t have the right systems in place, it’s much harder to recover when it does.”
Drawing from 40 years' experience working with global food processors, JBT Marel experts, like Bardic, ensure processors have access to an extensive knowledge base. “We work with processors to provide solutions that meet specific processing needs but also to optimize system security. The key is to build in security at every level of production.”
Operations under attack – what’s the cost?
The cost of prevention compared to the cost of recovery makes a compelling case for cybersecurity investment.
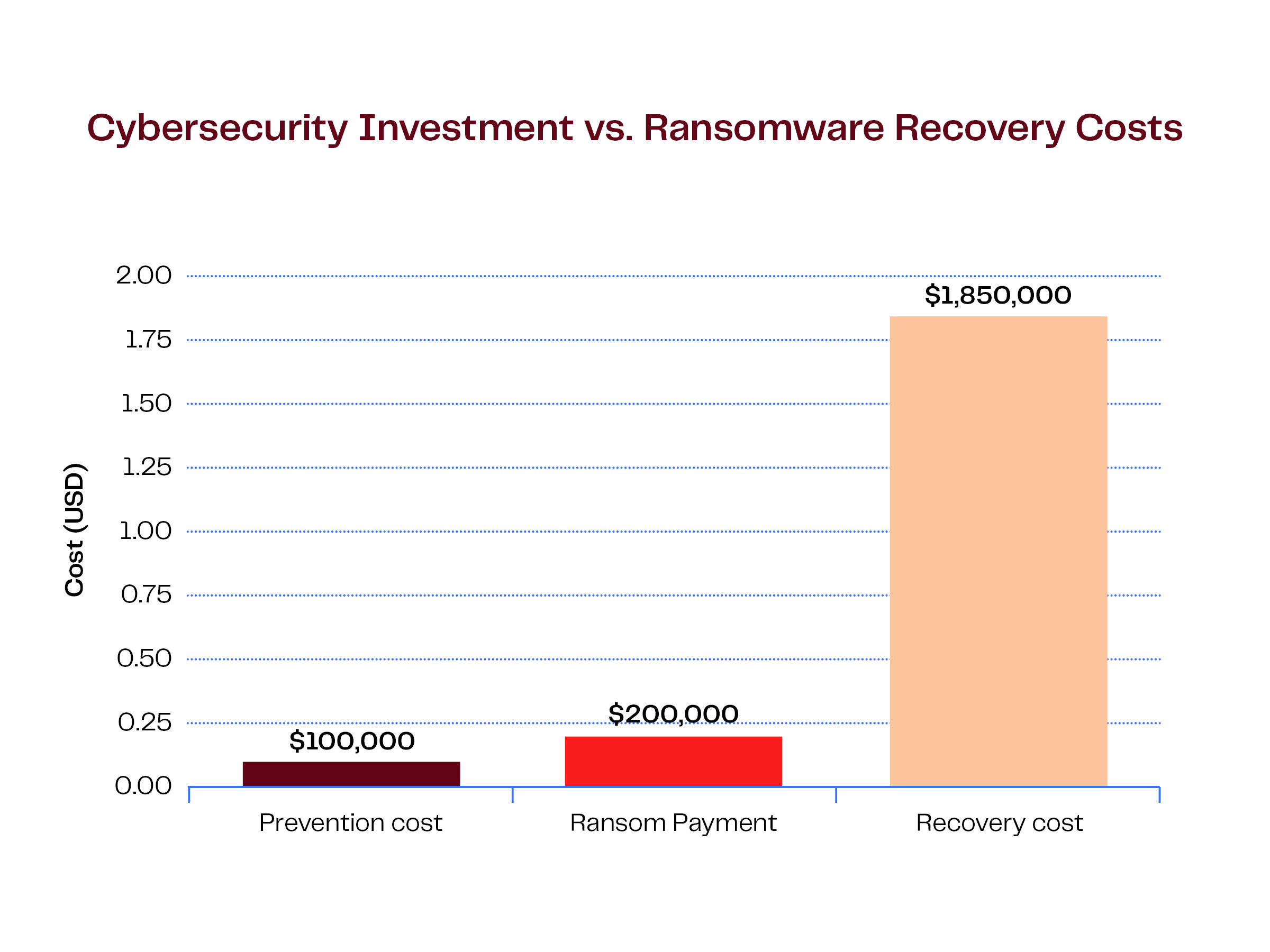
Case study: A poultry processor, processing 1 million birds weekly, packaging over 360,000 end product units daily. The ransomware attack lasts for 12-hours, with OT systems targeted including plant floor scheduling, weigh scales, and labeling. The attack stops production across two shifts. It is a partial disruption which blocks around 250,000 units. The cost, direct production downtime cost per hour $25,000 - $40,000, estimate up to US$ 546,000 in lost output, rework and recovery, consequence to employees.
Building a multi-layered defense approach
Crisis planning and preparedness is key to either preventing an attack, or if the worst happens, minimizing its effect. With a solid, practiced, well-communicated plan in place, businesses recover faster, and see less impact on business operations and finances, and the mental health of their people.
Effective cybersecurity for food processors requires multiple protective layers.
Network segmentation
Think of your business network as a house with glass walls between rooms. You can see and communicate between areas, but if bad actors break into one room, they can be isolated. This means manufacturing might continue running even if business systems are under attack.
Backup systems
Not all backups are equal. The speed of your recovery depends on your backup strategy:
- Snapshot systems enable faster recovery of recent data
- Cloud-based backups provide off-site protection
- Air-gapped backups remain isolated from network attacks
- Cloned hard drive
- Physical backup server
Both equipment and software play a crucial role in network segmentation strategies. Which is why JBT Marel design systems that can operate within segmented network environments, allowing critical production equipment to maintain functionality even when administrative systems are compromised. When planning segmentation, we work with you to understand how our equipment and software can best support your security architecture.
Staff training
Human error can be the cause of many attacks, regular training helps employees recognize phishing attempts and suspicious activity, understand how to minimize risks of credential theft, etc., and feel confident of their role in the case of an attack.
Incident response planning
Having a tested, practiced plan means making clear decisions during a crisis instead of panic-driven choices. Plans should cover:
- Immediate response procedures
- Communication with stakeholders
- Recovery priorities
- Legal and regulatory requirements
Smart outsourcing
For businesses who don’t have a dedicated IT security team; by working with a specialist cybersecurity firm, you can ensure a strong defense system and the support to get through a crisis:
- Expert assessment of current vulnerabilities
- Tailored security architecture for your specific needs
- Ongoing monitoring and threat detection
- 24/7 response capabilities
Just as when choosing processing machinery, when choosing security partners research is crucial. Check certifications and experience, look for firms with food industry knowledge who understand both IT and OT environments, and speak to peers.
Regulations around cyber security
Governments worldwide are implementing and increasing data security standards and regulations, including the NIS2 in the EU and EEA, and the Critical Infrastructure Designation (CID), to safeguard critical supply chains, including the food supply chain. While frameworks such as NIST Cybersecurity Framework in the US and ISO/IEC 27001/2002 globally, present a way for businesses to build secure systems.
Building security culture
With artificial intelligence tools set to accelerate both the attack and defense capabilities it is more crucial than ever for processors of every size to examine their cyber security.
- Evaluating security when selecting new equipment or software
- Requiring security standards from suppliers and partners
- Regular security reviews and updates
- Open communication about threats and solutions
By embedding security thinking into every business decision, food processors can ensure they will be here to participate in the future of the industry.
Explore more about security systems and protocols here.
Breaking the habit of silence
Food processors face a dilemma when attacked, stay silent or speak out. The instinct to hide what happened is understandable, no business wants to reveal weaknesses which may open them up to further attacks, or have suppliers and customers cancel contracts.
On the other hand, by staying silent the industry is denied intelligence about threats, tactics, and effective defenses. The criminal ransomware organizations exploit this silence, using the same methods across different companies who have no opportunity to learn from each other’s experiences.
In the US food and agriculture sector 167 ransomware attacks were reported in 2024, with most companies describing incidents as ‘tech issues’ rather than cyberattacks. In the UK, recent government data shows cyber incidents affected 32% of small businesses, 50% of mid-sized businesses, and 69% of large businesses.

The food supply chain is complex, an attack on one processor affects farmers, distributors, retailers, market prices, and consumers. Being targeted doesn’t indicate negligence, but that your business is part of critical structure ideal for ransomware attackers to make fast profits.
By being transparent about attacks businesses along the food supply chain remove the shame of a failed system and enable industry learning and strengthening, taking back power from criminal organizations. The question isn’t whether your company will be or was attacked, but whether your business and the industry will be stronger because of how you handled it.
One bitten, twice shy – are there any positive results from ransomware attacks?
Let’s be honest, it can be hard to find a positive to a ransomware attack. But, if viewed from the point of view of having a stronger company in the future, the positives are there. In the aftermath, building a more resilient security network is prioritized, with every employee and team onboard with changes and investments needed. And, if handled correctly, businesses can increase solidarity and empathy with the IT team, along with improving overall communication.
Transparency in the response process is increasingly important—not only to maintain trust with stakeholders, but to meet legal disclosure obligations and ensure compliance with cyber insurance requirements.
A ransomware attack can ultimately result in a stronger company culture and a more resilient business.
But, maybe the best idea is in prevention
Ransomware attacks on food processors are more than possible, they are inevitable. But being targeted doesn’t equal powerlessness. Effective preparation with comprehensive cybersecurity strategies, you can change the narrative from victim to success story, and build the digital resilience needed to thrive in the digital age.
At JBT Marel, we believe cybersecurity is not just an IT concern, it’s a production imperative. Through the combination of in-depth industry knowledge and the guiding structure of ISO27001:2018 we are constantly working to ensure our processing systems, software and hardware help safeguard your OT and IT environments.

The investment in cybersecurity may seem like paying for the invisible, but the protection it provides has very visible outcomes. In an industry where margins are tight and disruptions are costly, the businesses that survive and thrive will be those that recognize cybersecurity as essential infrastructure that ensures operational continuity, not an optional expense.
Ransomware is a growing threat to the food processing industry. Protecting operations starts with resilient systems and informed strategies. If you’re ready to strengthen your production security, we’re ready to help you. Discover how JBT Marel’s secure systems support resilient operations and help protect your business from digital threats. Together, let's build a safer, smarter food supply chain.